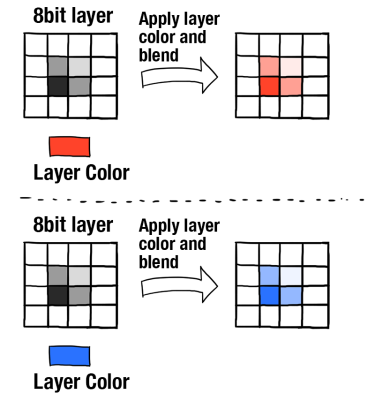
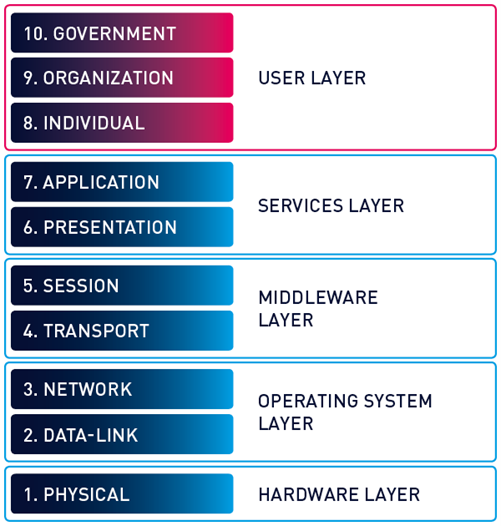
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
5
(706)
Write Review
More
$ 24.00
In stock
Description
Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i
Networking Basics: The OSI Model
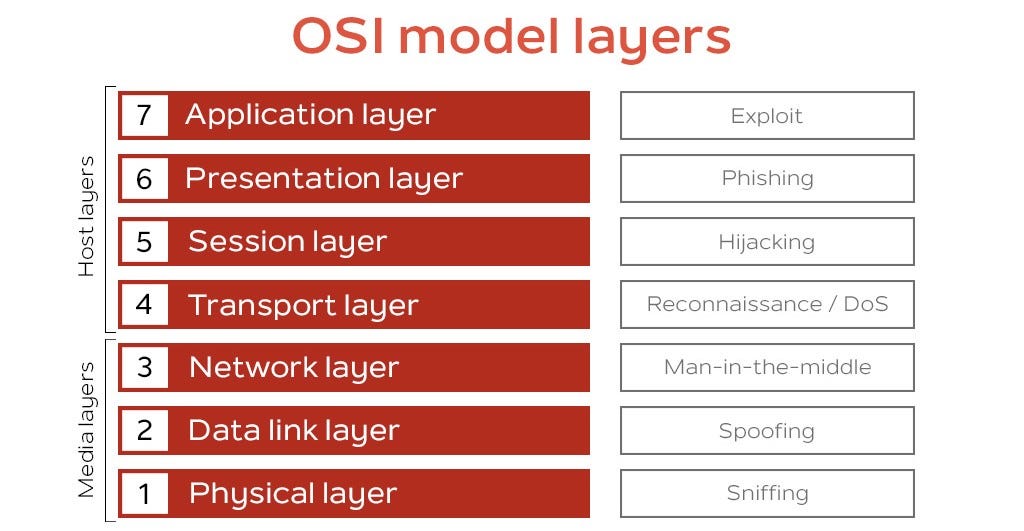
Cyberattacks On The OSI Layers, by MSBJ

Common Security Attacks in the OSI Layer Model

Security Threats at OSI layers
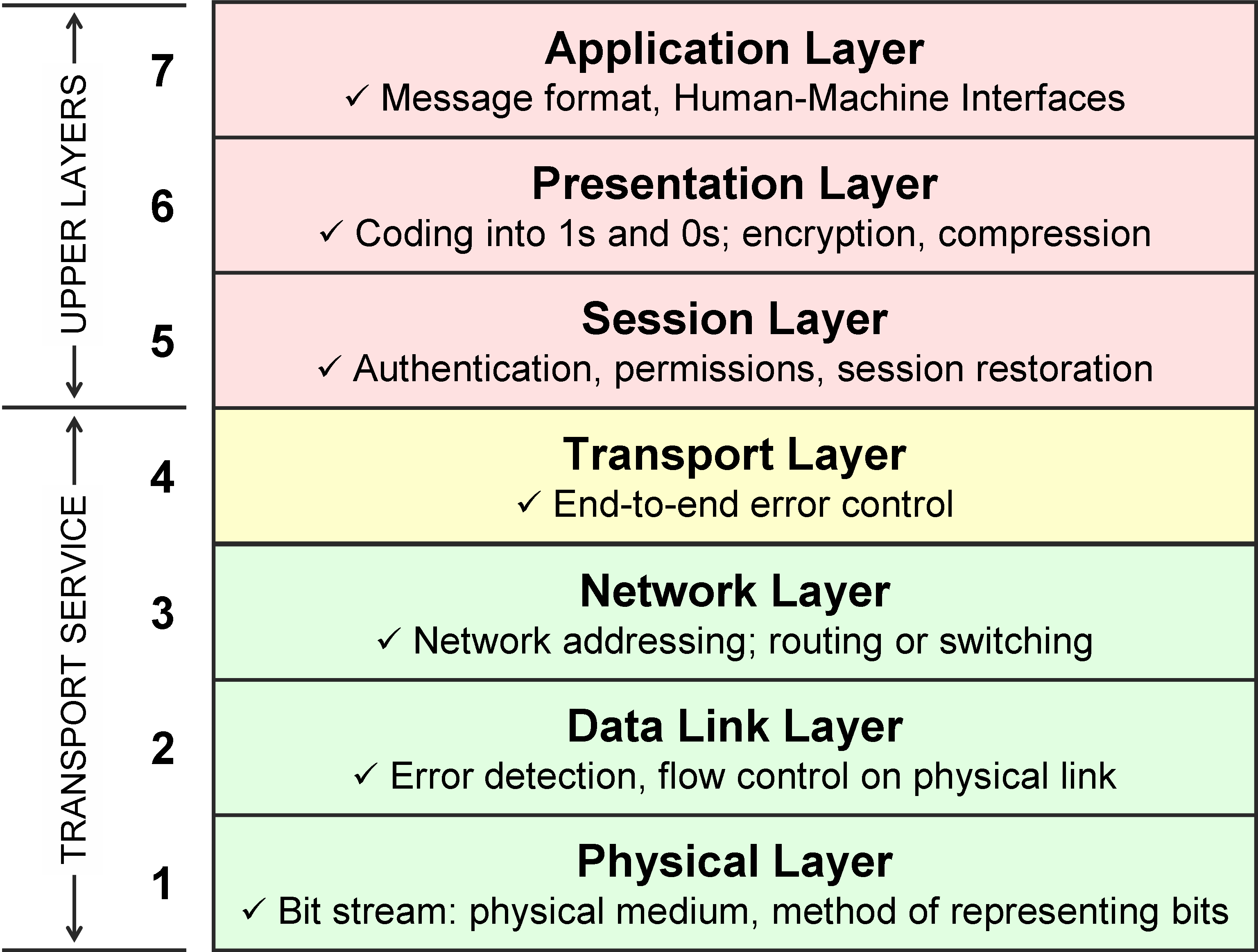
osi model explanation
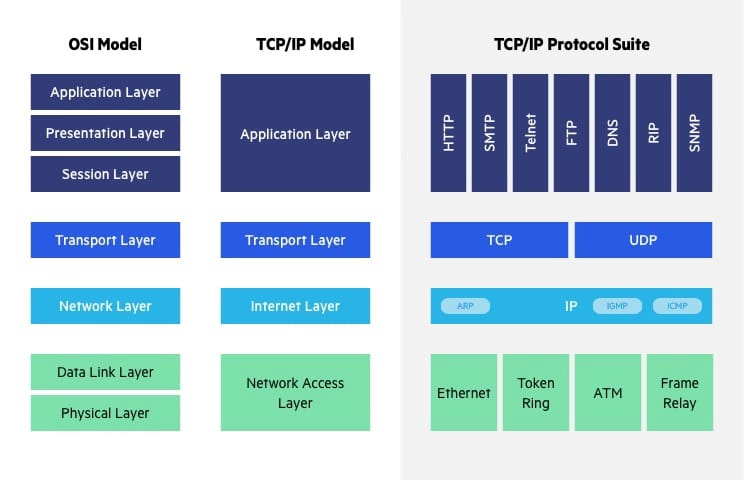
Glossaries learnonline
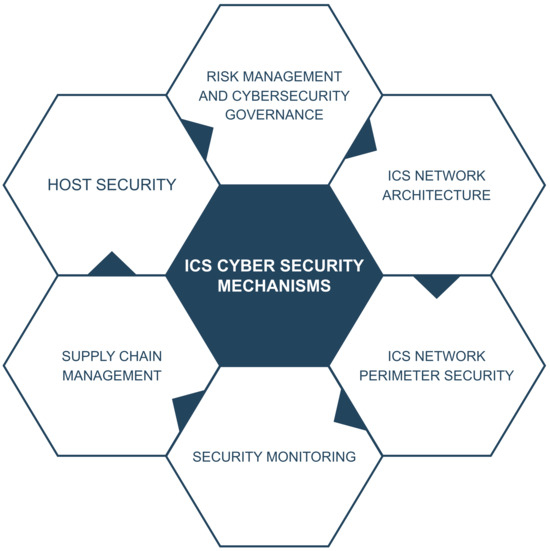
Sensors, Free Full-Text

Electronics, Free Full-Text

Intrusion Detection and Prevention

Seven Layers of OSI Model in an easy way

Practical Cybersecurity Architecture - Second Edition

Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

A survey of cyber security threats and solutions for UAV
You may also like