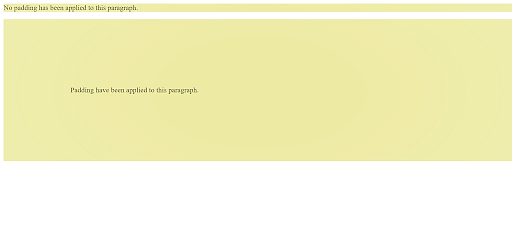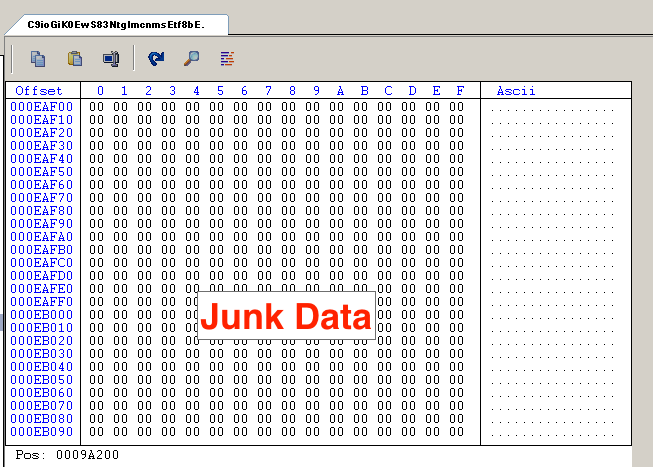
How Hackers Use Binary Padding to Outsmart Sandboxes
Make your First Malware Honeypot in Under 20 Minutes

Top 10 Linux Server Hardening and Security Best Practices - Intezer

Disarming visualization-based approaches in malware detection systems - ScienceDirect

Czesia Glik on LinkedIn: How Hackers Use Binary Padding to Outsmart Sandboxes and Infiltrate Your…

Emre KISA on LinkedIn: Indirect prompt injection, have you heard

Detect Malware Associated with the Most Exploited CVEs - Intezer

2024 Healthcare Cybersecurity Trends - Blue Goat Cyber
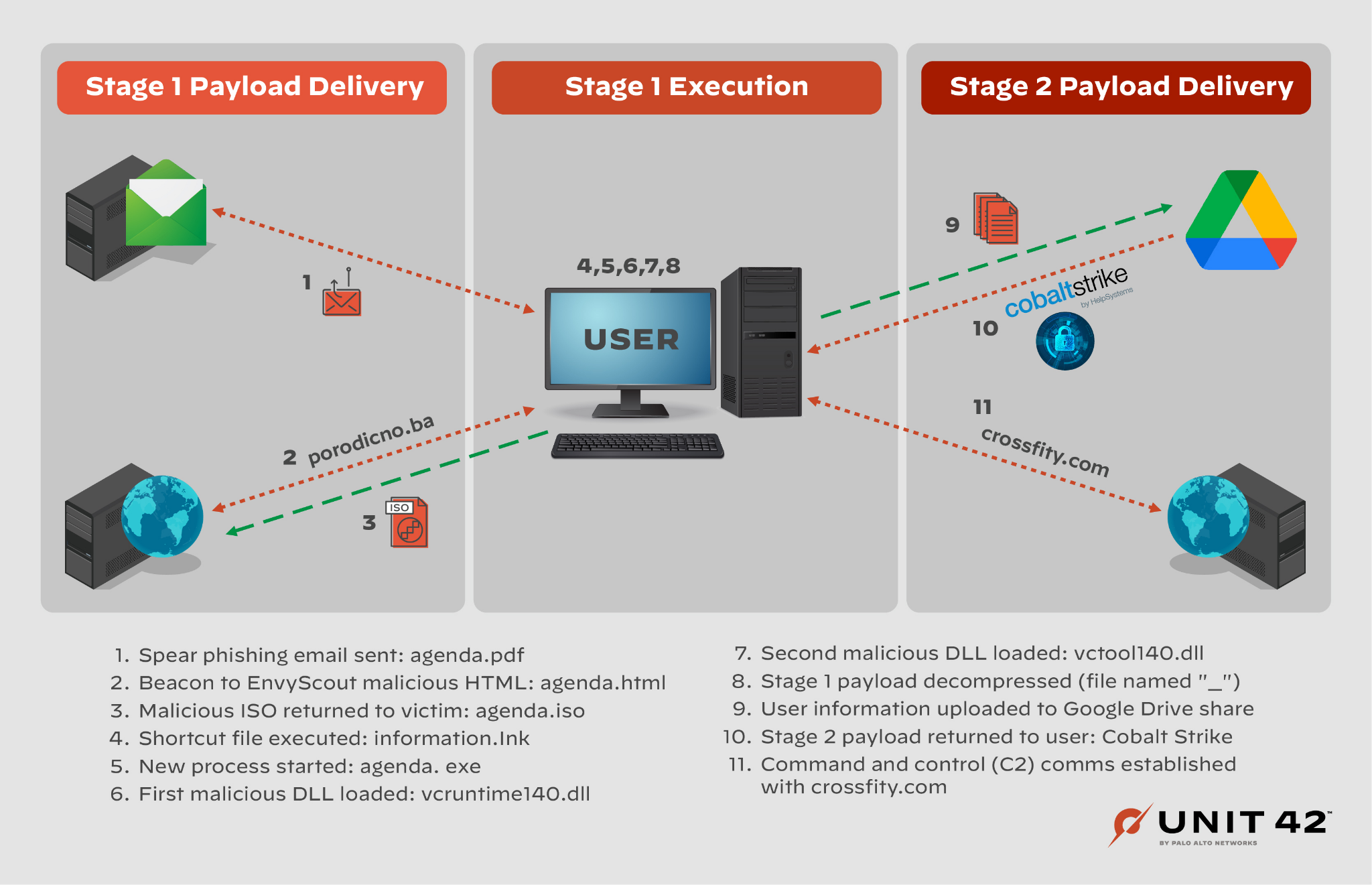
Cloaked Ursa (APT29) Hackers Use Trusted Online Storage Services

Roy Halevi (@royhalevi) / X

How can Advanced Sandboxing Techniques Thwart Elusive Malware? - Wiadomości bezpieczeństwa

Gray Hat Hacking: The Ethical Hacker's Handbook [2nd edition] 0071595538, 0071495681, 1211471691, 9780071595537

How Hackers Use Binary Padding to Outsmart Sandboxes

Intezer on LinkedIn: How Hackers Use Binary Padding to Outsmart

نشر Emre KISA على LinkedIn

Emre KISA on LinkedIn: Indirect prompt injection, have you heard